ARM TrustZone Emulation with QEMU
An easier way to try this mechanism is to let you use it in your work environment thanks to the emulation.
Explaining the ARM TrustZone
The ARM TrustZone, also known as the ARM Security Extensions, encompasses optional hardware security features introduced since ARMv6. These extensions define security functionalities for not only the ARM processor but also various components within an ARM SoC. Essentially, ARM Security Extensions establish a clear separation between two distinct worlds, Secure and Non-Secure, inside a single SoC. This segregation enables robust hardware-based isolation between software operating in the regular (Non-Secure) world and the Secure world, eliminating the necessity for dedicated security hardware. Typically, a device will run its mainstream OS like redpesk OS in the Non-Secure world, while simultaneously operating a specialized secure OS and its applications in the Secure world.
The isolation between these two worlds is primarily managed by an additional security state integrated into various aspects of the architecture. On the ARMv8 Instructions Set Architecture (ISA), a solitary secure state bit governs accessibility to specific system registers and memory, and determines where interrupts should be directed. Likewise, devices on the bus can be configured as Secure or Non-Secure, offering defense against unauthorized access.
You can find more details on the official ARMv8 documentation.
Emulation with QEMU
Some concepts in theory
The integration of ARM Security Extensions into QEMU’s ARM target aims to facilitate the development of secure software, eliminating the need for specialized hardware. This support allows to seamlessly load trusted Secure world binary alongside redpesk OS operating in the Non-Secure realm, enabling comprehensive interaction while debugging both environments. The addition of OP-TEE* further enhances this capability by providing a secure execution environment for Trusted Applications, complementing the functionalities offered by ARM Security Extensions. It could be relevant for critical embedded environments such as avionics or automotive.
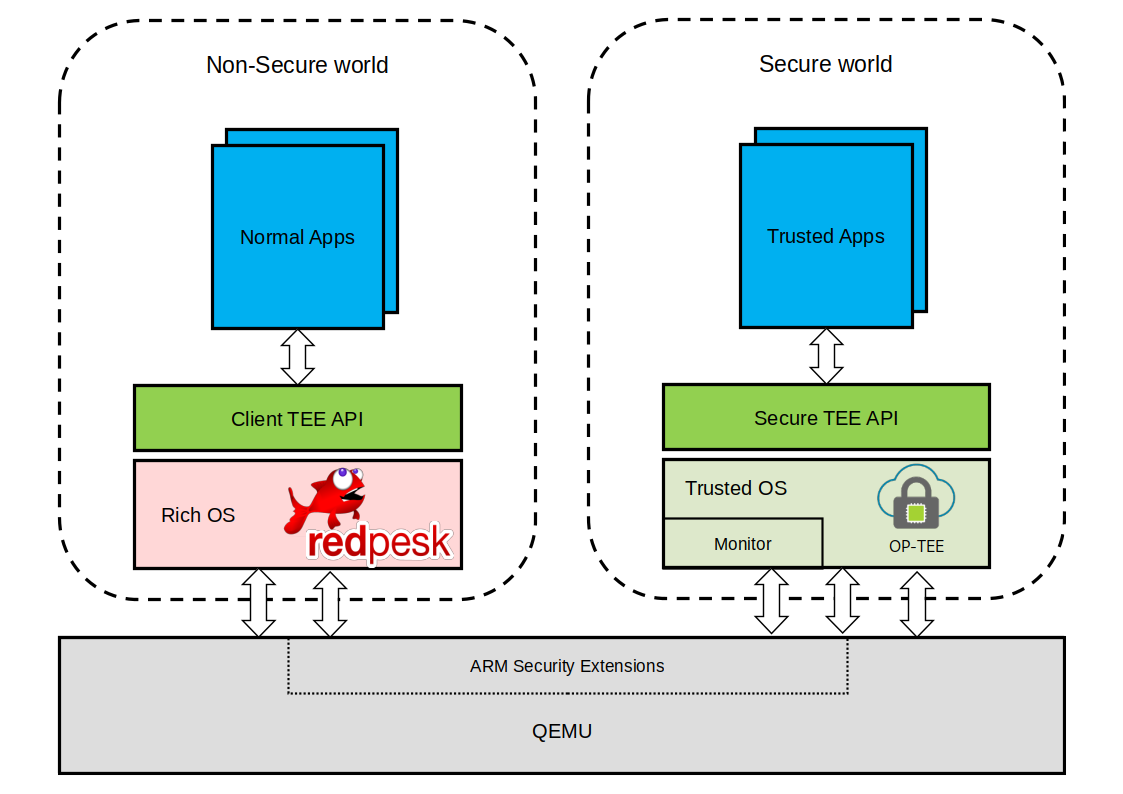
To sum up, the integration of ARM Security Extensions, coupled with OP-TEE, enables the simultaneous operation of distinct Secure and Non-Secure software within QEMU. QEMU emulates the ARM based architectural components that bridge these two domains, while OP-TEE provides a trusted environment for executing secure applications. It’s worth noting that while QEMU has made strides in supporting various ARM architectural features, including 64-bit and ARMv8-A, it appears that it lacks some support for ARM Security Extensions yet. Attempts to use features like the SMC instruction** or secure registers may result in undefined operation failures.
Practicing the emulation
Deploying an example of an emulated ARM TrustZone could be nice for a better understanding.
The IoT.bzh team is currently interested in the study of this feature but you can find dedicated articles on the web such as some articles like this one to discover the ARM TrustZone on QEMU.
NOTES:
*: the OP-TEE is a Trusted Execution Environment (TEE) developed to work alongside a non-secure Linux kernel running on Arm Cortex-A cores, utilizing TrustZone technology. OP-TEE employs TEE Internal Core API v1.1.x for interaction with Trusted Applications, and TEE Client API v1.0 to facilitate communication with a TEE. These APIs are outlined in the GlobalPlatform API specifications. Sources: ARM reference documentation
**: SMC means the Secure Monitor Call. It’s simply a mechanism that allows a Normal world application to request services or interact with the Secure world. More details here.